Build Momentum with Practical No‑Code Systems
Today we dive into No-Code Small Business Systems: pragmatic ways to replace scattered spreadsheets, manual copy‑paste, and costly custom software with visual tools you can deploy in days. Expect stories, checklists, and honest lessons from shops, studios, and service teams growing lean. Share your wins, ask questions in the comments, and subscribe for weekly playbooks, templates, and step‑by‑step experiments you can apply before your next customer walks in.

Map What Matters First
Before touching any tool, trace how value moves through your business, from the very first inquiry to money in the bank and a delighted customer. This clarity prevents shiny‑object chaos, reduces rework, and keeps your no‑code stack intentionally small. You will discover hidden waits, duplicated effort, and data you never needed. Capture quick wins, document assumptions, and invite frontline teammates to challenge the flow with real stories and numbers.

From Leads to Loyal Customers
Turn scattered inquiries into a calm, visible pipeline that nudges prospects forward without nagging or guesswork. With a lightweight CRM built on a table, forms, and automations, you can centralize data, standardize follow‑ups, and never forget who needs help next. Celebrate small moments, like a warm reply after a timely reminder. The result is fewer leaks, faster decisions, and service that feels personal at any volume.
Automation That Frees Time Without Losing Control
Automate repetitive tasks, not judgment. Link your source of truth to calendars, email, documents, and chat so work advances quietly in the background. Keep humans in the loop at key checkpoints, and log every change. Start with a very small set of high‑impact flows. Review metrics after a week, then tighten, simplify, or delete. Velocity comes from confident pruning, not from adding yet another bot.

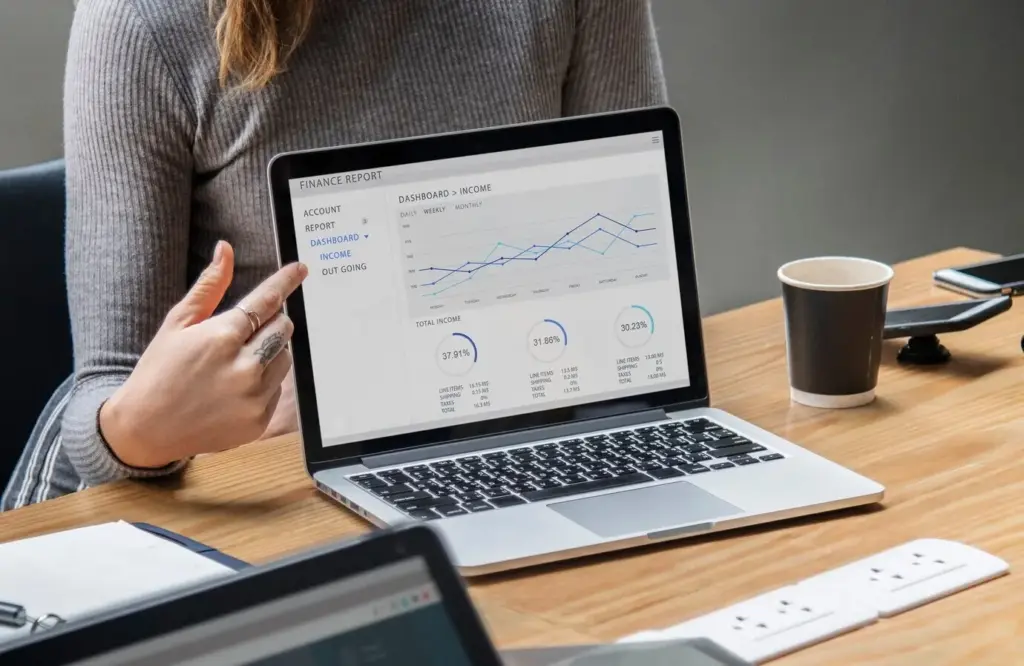
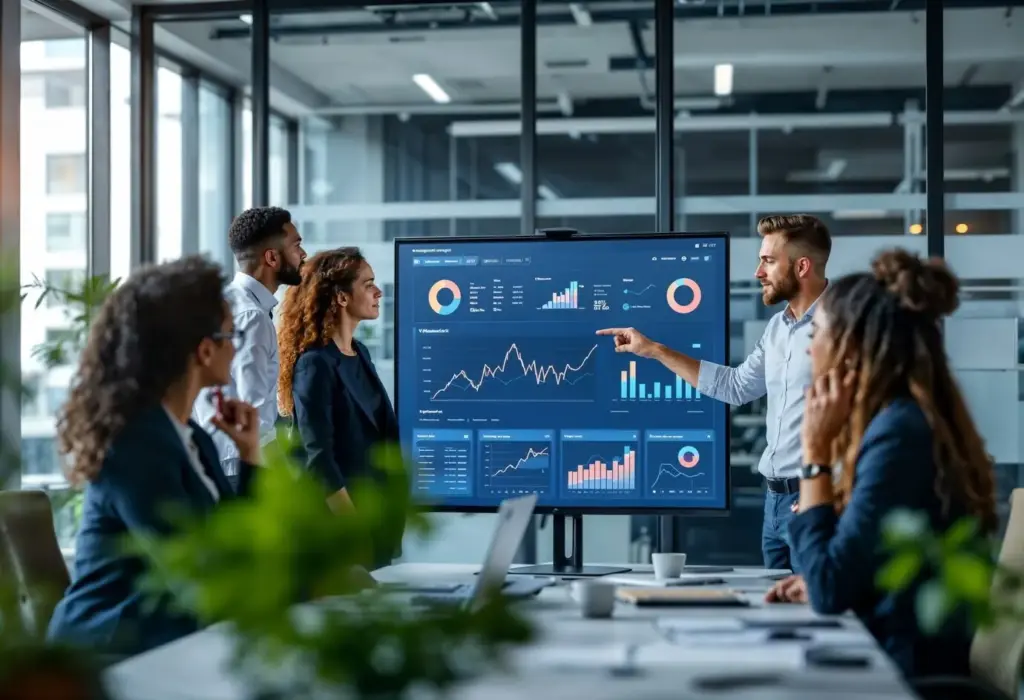
Data You Can Trust and Actually Use
Metrics matter only if they drive decisions. Centralize clean data, define how it is created, and surface it in dashboards that answer real questions. Keep vanity counts off the front page. Tie every chart to an action you are willing to take. When numbers disagree, investigate field definitions, not people. Document calculations in plain language. Clarity turns numbers into alignment, and alignment turns into faster, better execution.

Design a Delightful Customer Journey
From first click to final thank‑you, craft interactions that are fast, clear, and reassuring. Use forms, portals, and messages that respect time, reduce uncertainty, and showcase your brand’s personality. The right details—progress bars, plain‑English copy, and flexible rescheduling—create trust. Pair automation with empathetic human checkpoints. When customers feel guided rather than pushed, they buy again, refer friends, and forgive small hiccups because the relationship feels genuine and attentive.
Governance, Security, and Sustainable Scale
As systems grow, small decisions compound into either dependable reliability or fragile complexity. Set roles, approvals, and audit trails early. Back up data, version automations, and test changes in sandboxes. Keep sensitive records encrypted and access‑scoped. Periodically delete what you no longer need. Establish a cadence for reviews so you adapt to new regulations and vendor changes. Good governance is invisible daily and priceless during surprises.
Access and approvals with intent
Define roles for admins, builders, and contributors. Restrict sharing to named groups, not ad‑hoc links. Require approvals before messages go outside the company. A clinic protected privacy by limiting patient fields to authorized roles while allowing schedulers to work quickly. Log actions, rotate keys, and use single sign‑on when possible. Security is cultural as much as technical, so explain the why behind every permission choice.
Backups, versioning, and testing
Schedule automated exports, keep off‑platform backups, and label versions clearly. Duplicate your workspace into a sandbox to test flows before they touch customers. Run simulated orders and failure cases, like missing fields or API downtime. A boutique avoided a launch‑day fiasco by catching an email loop in staging. Write rollback steps you can follow under stress. Confidence grows when recovery is rehearsed, not imagined.
When to call in a specialist
Bring in certified builders when integrations get complex, data volumes spike, or compliance matters rise. Ask for architecture diagrams, change logs, and knowledge transfer sessions so your team stays empowered. Negotiate maintenance windows and response times. A nonprofit saved costs by co‑building alongside an expert, then taking over. Share your hiring questions or partner recommendations in the comments, and subscribe for a vetted directory update next month.